For additional information about Acceptance Research click here.
Recent events in Kenya should prompt development professionals to realize what many in emergency response have already concluded through painful experience: that in order reach one’s development goals and meet a duty of care to one’s dedicated staff it is time to get serious about security management. We can no longer claim with any conviction that security management is unnecessary for development programs in non-conflict countries. Bolivia, Côte d’Ivoire, Myanmar, Nepal and Venezuela are all countries with extensive development programs that have either slid into conflict and chaos or currently hover on the precipice of insecurity. On the other side of the equation are nations emerging from conflict where new development initiatives have begun but the remnants of conflict remain (Kosovo, Liberia and Sierra Leone). Even in the best of times, many of these countries are plagued with poor infrastructure, treacherous road conditions and crime.
Development practitioners justifiably resist the imposition of onerous security regulations on their staff and operations for fear that such regulations will negatively affect successful programs. Perhaps this view is informed by an incomplete understanding of the range of security management alternatives available or by a reaction to an unfortunate experience where draconian security measures were imposed from above. In recent years security management approaches have evolved that are compatible with development prerogatives and actually enable development programs to continue to be effective in the most complex, insecure environments.
Security strategy
Three distinct approaches to security management offer a range of options for developing an effective security strategy. The protection approach employs technologies and procedures that reduce organizational exposure to threats – “hardening the target.” Examples of protective measures include installing locks, window grates and security lighting, erecting high compound walls, using armored vehicles and establishing facility access procedures. The deterrent approach uses counterforce to intimidate or deter aggressors in order to negate the threat. Examples of deterrent measures include use of military and peacekeeping forces, threat of violent reprisals, economic sanctions and withdrawal of services. The use of armed escorts and armed guards falls into this category. The third approach, acceptance, is based upon developing relationships and gaining consent from beneficiaries, local authorities, belligerents and other stakeholders for organizational program operations as a means of reducing or removing threats.
Gaining acceptance among stakeholders is directly related to an agency’s mission and positive local perceptions of the organization and its staff. Local perceptions are influenced by project design and accountability, agency adherence to transparent principles and staff behavior that respects cultural norms.

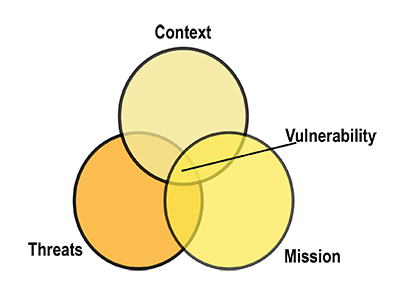
An organizational security strategy is derived from the combination of approaches an organization applies within a defined operational context. In developing a particular security strategy, one must first consider the organizational mission and programs to be implemented. Factors that define operational context include: understanding the overall operational environment, demographics, history, economy, and other similar factors; identifying key stakeholders and the dynamics of power and influence, motivation and intent; assessing and prioritizing likely threats; and analyzing risk and the organizational risk threshold. A particularly important element of this context is the range of likely safety and security threats in the operational environment. When one determines the type and scope of proposed program activities and how the identified threats might impact the relative vulnerability of personnel, assets and programs, then an appropriate, effective security management strategy can be derived.
Acceptance
In order to provide development assistance, organizations strive to establish and maintain effective relationships with local partners, communities and influential leaders. Because the acceptance approach to security is consistent with this relationship-driven development approach (albeit with some elements of the protective approach applied as the threat environment warrants), it is usually the cornerstone of effective security management in a development context.
Sustainable development programs are often designed to address beneficiary needs in a manner that fosters transparency, accountability, local participation and empowerment. These very same values are the hallmark of the acceptance approach to security. The responsibility of each staff member is to strive to understand the host culture and behave in a manner that respects the cultural norms while remaining vigilant to any changes in the operational environment that might increase individual and/or program exposure to threats. In this way the acceptance approach dovetails nicely with development program approaches and is neither onerous nor expensive to implement. The acceptance approach is not a panacea for addressing all security threats, but it provides a foundation for effective security management for development organizations.
Security management system
Through a security approach (or combination of approaches) an organization determines a security strategy, and the strategy informs the operational security management system. Feedback from many development managers over many years has highlighted the following basic components of a functional security management system, each of which is discussed in further detail below:
- information gathering, analysis and dissemination;
- site selection and facilities management;
- personnel;
- communications;
- transportation;
- reporting and responding to security incidents; and
- security planning.
Information gathering, analysis and dissemination. A reliable means of gathering, analyzing and disseminating information is essential for effective program and security management. It allows an organization to establish and maintain a clear understanding of the operating context and changing threat environment that influence how an organization should design and implement its development programs.
Needs assessments often address the operational context and local institutional capacities. They should also analyze the overall security environment. Doing so provides valuable insights for program design and implementation. It also helps identify the most appropriate approach to security management, which in turn affects proposals and budgets, and staff selection and orientation. Since the operating context is rarely static, a means of constantly gathering and analyzing information is essential. The availability of updated analysis allows program managers to keep staff well-informed, adjust program approaches, orientate new employees and brief visitors. Participatory assessments involving local partners, beneficiaries and organizations have the added benefit of building greater acceptance among these stakeholders.
Site selection and facilities management. Secure facilities establish a physical space that offers a productive work environment and provides access to constituents, beneficiaries and colleagues while maintaining the capability to prevent intrusion from undesirable elements and delay attack. An optimal mix combines positive local perceptions, physical construction and technology, and procedures consistent with the organizational mission.
An acceptance approach focuses on neighborly relations and culturally appropriate means of welcoming and screening visitors. In the face of increasing insecurity, more overtly protective measures may be instituted.
Personnel. All staff members should be selected, supervised and provided with appropriate training and support in an ongoing manner to fulfill their assigned responsibilities and to work effectively and safely in their respective areas of operation.
Each staff member plays a pivotal role in developing and maintaining positive relationships with the various stakeholders in an operational area. Local people often ask drivers and guards about the organization’s motives, programs and potential opportunities. Are these cadres of staff sufficiently informed and empowered to accurately explain your organization’s development mission, program activities and to refer inquiries appropriately? Are staff selection and orientation designed to ensure that staff behave and communicate in a respectful and culturally appropriate manner?
Communications. Successful security management relies on effective communications. While technology is important in facilitating communication, the procedures by which messages are developed, delivered and confirmed under difficult conditions are the essence of effective communication.
Every environment presents unique challenges to effective communications. In many developing countries, communications infrastructure is weak or unreliable. Determining the most appropriate combination of communications technology and providing staff with the relevant training to use the technology is key to effective program management and security.
Communications with local stakeholders should be clear about what the organization represents and provide an avenue for local feedback. This allows an organization to manage its profile and maintain stakeholder consent.
Transportation. Organizational personnel are at greatest risk of accident, assault and detention while traveling. Transportation policies, procedures, equipment and training should address the risks associated with dangerous road conditions, banditry, hostile checkpoints, land mines and other transportation-related threats. Road accidents remain a major cause of injury and death for development workers. Vehicle choice and maintenance, driver training, appropriate policies and procedures all contribute to reducing staff exposure to transportation risks. Personnel should be instructed to drive in a manner that is safe and respectful of pedestrians in order to foster a positive organizational image and gain acceptance.
Reporting and responding to security incidents. Collecting, analyzing and sharing incident report data is essential to good project management and decision-making. Better understanding of incident factors, patterns and trends contributes to improved security planning, staff training and resource allocation. Each organization should develop clear reporting and post-incident staff support protocols, and, to the extent possible, share incident report data internally, with partners and other NGOs.
Security planning. Security planning is an ongoing consultative process that involves a broad range of agency staff and external personnel. It defines the threat environment, sets forth agency policies, procedures and staff roles and responsibilities, and provides guidance for responding to likely contingencies in an accessible, user-friendly manner.
Conclusion
Experience reminds us that even for development programs, the operational environment rarely remains static. Seemingly stable countries can descend quickly into insecurity.
Given the constant flux of political fortunes, increasing crime and insecurity, it behooves development organizations to take a hard look at their security management systems.
The acceptance approach provides a foundation for effective security management that is consistent with the values that underpin development: relationships based on mutual respect and effective communications. For the sake of dedicated staff and for the continuation of valuable programs that benefit partners and beneficiaries, effective security management in a development context is a must.
In addition to his work in the security sector, the author also has spent well over a decade working in the field on development projects.




Leave A Comment
You must be logged in to post a comment.